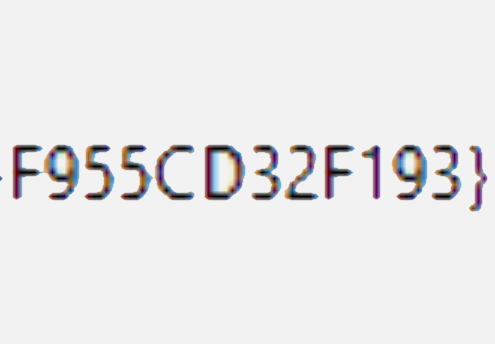
I have a have been puzzling over a problem where I need to create one-time keys to access a system. My question is, is this secure to use a Globally unique identifier or GUID for this key. The consensus is generally yes.
While section 6 “Security Considerations” of the RFC 4122 standard states
Do not assume that UUIDs are hard to guess; they should not be used as security capabilities (identifiers whose mere possession grants access)
For the particular use case there appears to be a consensus in the community that this is “secure enough”, it is used every day whenever you get a link in an email to reset you password. They typically use a Guid to identify the request, and as the Guid becomes invalid once it has been used, even if someone did steal your id, it would only be good for one request assuming it has not timed out (many services have a timeout of 30 minutes for these Guids to be used) or already been used which would cause the authentication to fail.
Guids are also apparently guessable because they are designed for uniqueness (i.e. using the current date and MAC address of the machine as the seed) to produce a 128-bit integer, this makes the identifier predictable which could be a problem. A problem which is easily overcome by doing a simple trick used in cryptography, add a random salt, using a cryptographically strong randomization. A person could predict the Guid potentially, but more unlikely to predict the Guid and the random value. Then if you add in Transport level security of sending the information over SSL to prevent someone listening in (though if it is being sent it is being used so would be immediately invalid).
Sources
- IT Security: Are GUIDs safe for one-time tokens?
- StackOverflow: Is using a GUID security though obscurity?